Developing mobile-based solutions similar to facial recognition in iPhone, Android Face Unlock and IRIS Scanner. Cover various purposes such as mobile device security, payment authentication, and personalized marketing.

Facial Recognition Software AI Development Services
Take advantage of real-time monitoring capabilities and protect your assets with unmatched accuracy thanks to artificial intelligence technology for face recognition software made by Devox. Our engineering team delivers tailor-made solutions designed to meet your unique requirements, integrating seamlessly into your existing security infrastructure.
What is Facial Recognition Software and How Can it Help My Business?
Real-time facial recognition software is a technology that identifies and verifies a person's face from a video or live feed instantly. It can help radically boost your security system: you’ll quickly identify if someone who enters your premises is authorized or if they pose a potential threat.
Face recognition solutions can also streamline your access control, making it faster and more efficient for employees to enter secure areas without needing physical keys or badges. As a side benefit, it can improve customer service by recognizing returning customers and providing personalized experiences. By implementing this technology, your business can become safer without cost overhead or involving numerous technology solutions at once.
Facial Recognition Software Services We Provide
Artificial intelligence technology for face recognition algorithm serves a primary purpose for security means. Take a look at what can Devox provide both on the security side and in other realms of facial AI applications.
-
Mobile Facial Recognition
-
Cloud-based Facial Recognition Solutions
Identify individuals in real-time from video feeds or live events, useful for security, retail, and public safety applications without significant upfront investment in infrastructure. Cloud-based facial recognition operates through cloud platforms, providing scalable and accessible solutions with simple API integration.
-
Surveillance and Security Systems
Developing advanced surveillance systems that use facial recognition for enhanced security, including access control, visitor management, and threat detection in real-time. Within this service, Devox covers video surveillance, intrusion detection, and integration with other security components like access control systems.
-
User and Entity Behavior Analytics (UEBA)
These tools monitor and analyze user behavior to identify potentially risky or malicious activities within an organization. Understand and predict security threats based on behavior patterns, focusing on data analysis and anomaly detection.
-
1:1 (One-to-One) Verification Systems
Verify a person’s identity by comparing their live capture to a single image stored in a database for access control and authentication purposes, biometric authentication in banking, secure transactions, and device unlocking. Devox can build secure access systems for buildings, devices, and software applications.
-
Facial Recognition Search Engine
Building software that conducts facial recognition web search similar to PimEyes, TinEye or AI-based Clearview solution. Search and identify faces across the internet, analyzing specific features of a face from a submitted image and comparing them against a vast array of images available online to find matches.
-
Augmented Reality (AR) Applications
Facial recognition combined with AR can create interactive experiences by overlaying digital information on real-world images of faces. Such applications include virtual try-ons for glasses or makeup. The Devox developers can craft AR apps that boost customer engagement and retail experiences such as or similar to Instagram masks or virtual fitting rooms.
Benefits of Implementing Facial Recognition Software
Artificial intelligence technology for face recognition will bring one ultimate benefit of boosting your security level to the top.
-
Eliminate Unauthorized Access
Reduce the risk of unauthorized individuals gaining access to secure or restricted areas by several times. The practice of verifying identities through facial recognition will ensure only authorized personnel can enter certain premises, making it much harder for intruders to bypass security protocols.
-
Identity Theft and Fraud
Combat identity theft and fraud, especially in financial transactions and access to sensitive information. By matching faces with stored images in real-time, face recognition solution ensures that the person conducting a transaction or accessing information is indeed who they claim to be.
-
Prevent Tailgating
Tailgaiting is a common security breach in many organizations which facial AI tackles at once. Detect and alert security personnel if an individual follows an authorized person into a restricted area without proper credentials.
-
Boost Surveillance Efficiency
Gear up your surveillance systems by automating the detection and identification of individuals in real-time. You’ll minimize the need for constant manual monitoring of video feeds, allowing security personnel to focus on responding to identified threats.
-
Harness Large-scale Monitoring
For events or locations with large crowds, facial recognition can quickly identify known threats or persons of interest among thousands of faces, a task that is virtually impossible for human security teams to perform with the same level of accuracy and speed.
-
Improve Data Security
In the digital realm, facial recognition can secure sensitive data by ensuring that only authorized individuals can access certain information or systems, protecting against data breaches and cyber attacks.
-
Integrate with Other Security Measures
Facial recognition can be integrated with other security systems, such as access control, alarms, and security cameras, creating a comprehensive security solution that leverages multiple technologies for enhanced protection.
Key Functionalities to Add to Your Custom Facial Recognition Software
Accurate and Reliable Real-time Identification
The ability to identify and verify individuals in real-time as they pass through cameras, providing instant security checks without delays. It includes high levels of accuracy in identifying unique facial features, even in varying lighting conditions, angles, or partial obstructions like glasses or hats, ensuring reliable verification.
Customizable Matching Thresholds
Offers the ability to adjust the sensitivity of matching criteria, balancing between false positives and negatives to meet specific security requirements.
Multi-factor Authentication
Works as part of a multi-factor authentication system, combining facial recognition with other forms of verification like PINs, passwords, or physical tokens for enhanced security.
Diverse Database Management
Efficiently manages and updates databases of faces, enabling quick additions, deletions, or modifications as needed to keep the system up-to-date with the latest information.
Mobile and Remote Capabilities
Some facial recognition solutions offer mobile applications or remote access, enabling security personnel to monitor and manage the system from anywhere.
Privacy Protection Features
Includes built-in privacy protection measures, such as data encryption and anonymization, to ensure compliance with data protection regulations and safeguard individual privacy.
Analytics and Reporting
Provides analytics on access patterns, identification incidents, and other metrics, offering valuable insights for security improvements and decision-making.
Anti-spoofing Technologies
Incorporates technology to detect and prevent spoofing attempts, such as using photographs, videos, or masks to fool the system, ensuring that only live, real faces are recognized.

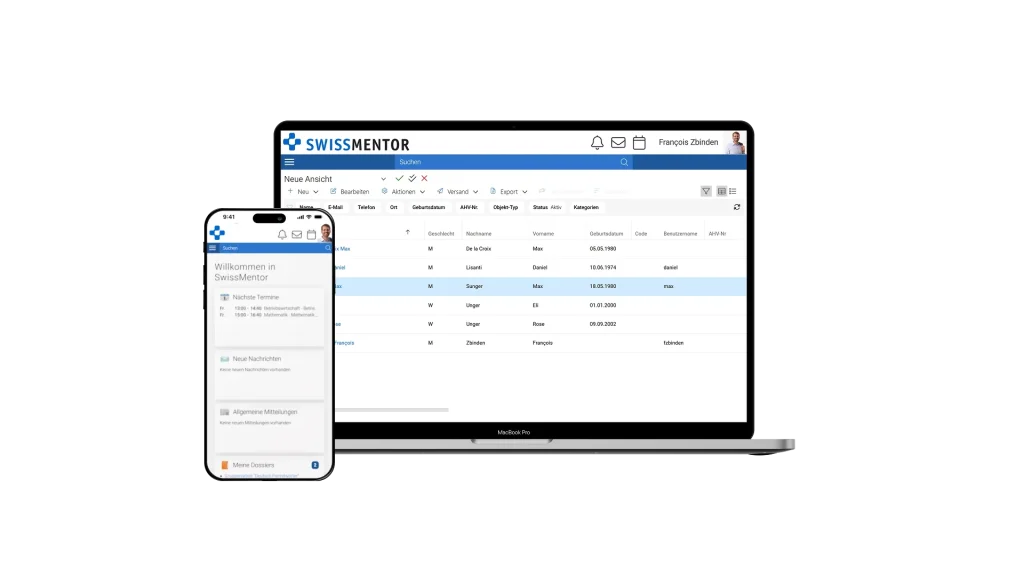
Modular LMS for Multi-Domain Learning: SwissMentor’s Enterprise-Grade Online Platform
A full-featured learning management system built to digitize education workflows, manage courses, and support online learning at scale.
Additional Info
- .NET Core
- PostgreSQL
- Angular
- Docker
- Kubernetes
- Azure
- SCORM
Switzerland

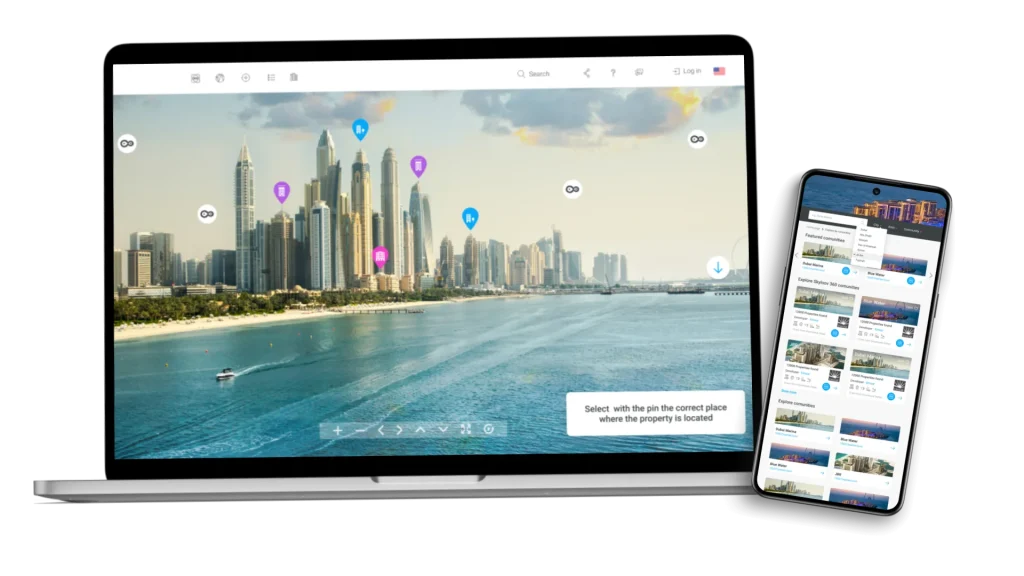
Immersive Property Portal with 360° View for Real Estate Buyers and Brokers
A real estate portal designed to streamline property search, simplify renting and buying decisions with personalized housing recommendations.
Additional Info
- NET Core
- MS SQL
- ELK
- Angular
- React Native
- NgRx
- RxJS
- Docker
- GitLab CI/CD
UAE

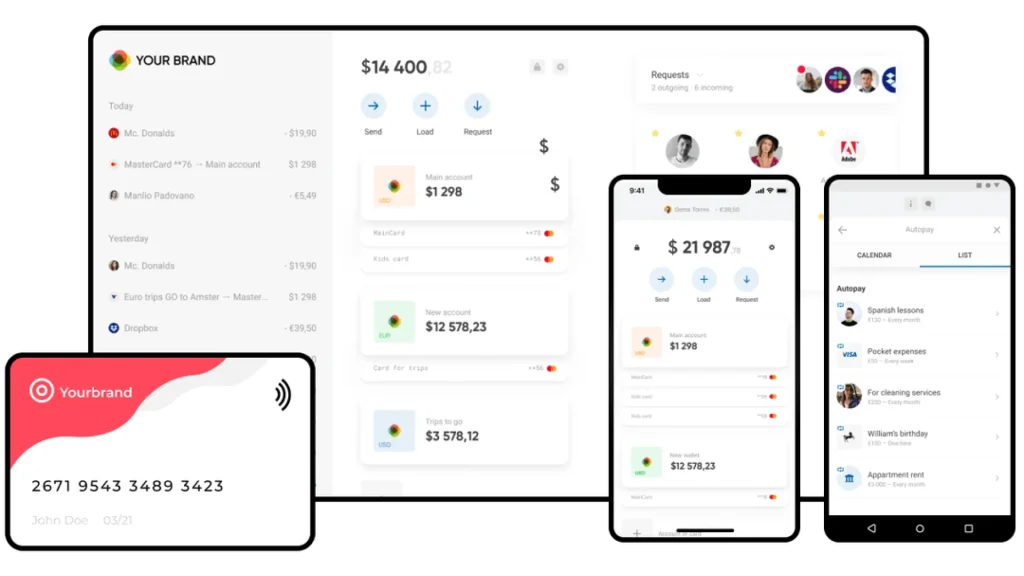
Web3 PaaS Ecosystem for Next-Gen NeoBanking, RegTech, and Secure Data Vaulting
A blockchain-powered PaaS ecosystem enabling financial providers to launch custom neobanking solutions with secure infrastructure.
Additional Info
- Blockchain
- .NET
- Node.js
- AWS
- Docker
- PostgreSQL
- React Native
USA
Trusted by
Industry Contribution Awards & Certifications
Testimonials
FAQ
-
What programming languages and technologies are used in developing facial recognition software?
We use a combination of programming languages and technologies to develop state-of-the-art face detection systems, including Python for its extensive machine learning libraries (e.g., TensorFlow, PyTorch), C++ for high-performance components, and JavaScript for web-based interfaces. Our development process leverages OpenCV for image processing, alongside deep learning algorithms to train accurate and efficient facial recognition models. This technological stack ensures our software is both powerful and versatile, capable of operating across various platforms and devices.
-
How does your facial recognition software comply with GDPR and other privacy regulations?
Compliance with GDPR and other privacy regulations is a cornerstone of our facial recognition software development. We implement strict data protection measures, including data anonymization, secure data storage, and encrypted data transmission. Our software includes features for easy consent management, allowing users to grant or withdraw consent for data processing. We conduct regular privacy impact assessments to ensure ongoing compliance and offer detailed documentation on data handling practices. Our approach prioritizes user privacy and regulatory compliance, minimizing legal risks for our clients.
-
What risk management strategies are in place for facial recognition software?
Our risk management strategy for artificial intelligence face recognition software includes multiple layers of security and operational safeguards. We conduct thorough risk assessments to identify potential vulnerabilities in the software and its deployment environment. Our software features robust encryption, access controls, and audit logs to protect against unauthorized access and data breaches. We also offer continuous monitoring and regular updates to address new threats and ensure the software remains secure against evolving cyber threats. Our team provides comprehensive training and support to help clients manage risks effectively.
-
How do you address false positives and negatives in facial recognition?
Minimizing false positives and negatives is critical for the effectiveness of facial recognition software. We utilize advanced machine learning algorithms and continuously train our models on diverse datasets to improve accuracy and reduce errors. Our software allows for adjustable sensitivity settings, enabling clients to find the right balance between security and convenience. We also implement multimodal biometric verification, combining facial recognition with other biometric methods (e.g., fingerprints) to enhance verification accuracy. Continuous software updates ensure our algorithms stay ahead of the curve in accuracy and reliability.
-
Can the facial recognition software operate in different lighting and environmental conditions?
Our facial recognition systems are designed to operate effectively across a wide range of lighting and environmental conditions. We use sophisticated image enhancement technologies to improve the visibility of facial features in poor lighting or adverse weather conditions. Our algorithms are trained on datasets that include images captured in various environments to ensure robust performance. Additionally, we offer infrared and thermal imaging capabilities for low-light or nighttime conditions, ensuring consistent accuracy and security 24/7.
-
How is the data collected by facial recognition software stored and protected?
All collected data is encrypted both in transit and at rest, using industry-standard encryption protocols. Devox stores data in secure, compliant data centers with strict access controls and regular security audits. Our software adheres to the principle of least privilege, ensuring that only authorized personnel can access sensitive data. We also provide data retention and deletion capabilities, allowing clients to manage data according to their policies and regulatory requirements.
Want to Achieve Your Goals? Book Your Call Now!
We Fix, Transform, and Skyrocket Your Software.
Tell us where your system needs help — we’ll show you how to move forward with clarity and speed. From architecture to launch — we’re your engineering partner.
Book your free consultation. We’ll help you move faster, and smarter.
Let's Discuss Your Project!
Share the details of your project – like scope or business challenges. Our team will carefully study them and then we’ll figure out the next move together.
Thank You for Contacting Us!
We appreciate you reaching out. Your message has been received, and a member of our team will get back to you within 24 hours.
In the meantime, feel free to follow our social.
Thank You for Subscribing!
Welcome to the Devox Software community! We're excited to have you on board. You'll now receive the latest industry insights, company news, and exclusive updates straight to your inbox.




































































