Table of content
Yet, too many organizations treat cybersecurity risk assessment as a formality — another box to check rather than a strategic pillar of business resilience. This mindset is a liability. In today’s hyper-connected world, security is not just about protecting data; it safeguards your operations, reputation, and long-term success. Whether you’re evaluating third-party vendors or strengthening internal defenses, a structured cybersecurity risk assessment methodology helps identify weaknesses before attackers do. Organizations around the world are using cybersecurity assessment services to streamline this process.
However, knowing what a cybersecurity risk assessment is is only the beginning. Whether you evaluate outsourcing vendors, secure cloud infrastructure, or fortify internal defenses, execution truly matters. This guide breaks down the essential stages of cybersecurity risk assessment — so you can move from passive defense to proactive security.
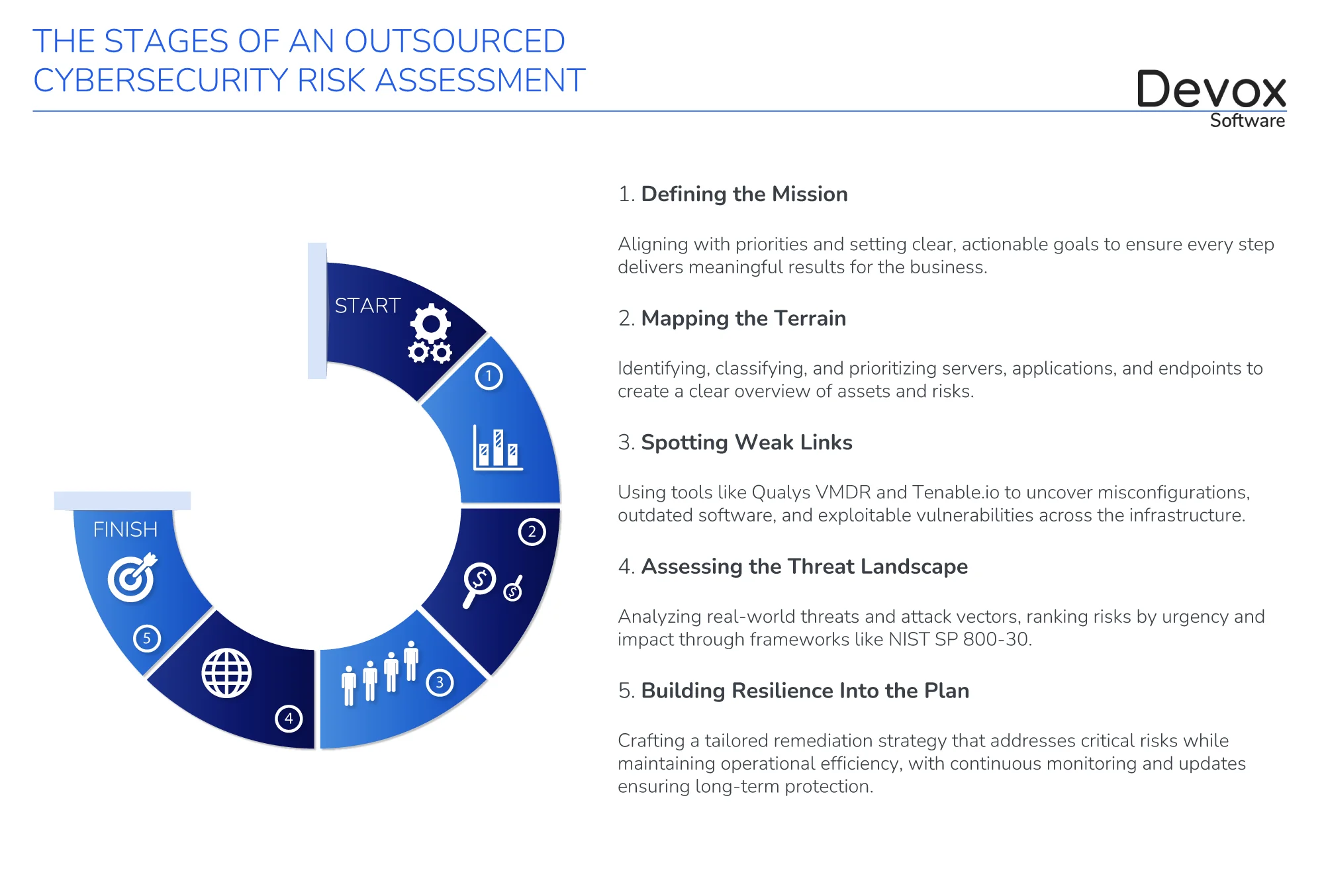
Stage 1. Define the Mission: Aligning Priorities
A cybersecurity risk assessment without a clear mission is like navigating without a compass — no matter how advanced your tools are, you’ll still get lost. Security efforts that don’t align with business priorities do more harm than good. They tie up resources, slow operations, and uncover critical vulnerabilities.
Before assessing risk, organizations need to define what’s essential. What are the most valuable assets — intellectual property, customer data, financial records? What threats pose the most significant risk? Where would a security failure be most devastating? Answering these questions lays the foundation for a targeted, highly effective cybersecurity strategy.
A clearly defined mission transforms cybersecurity from a compliance obligation to a business requirement. Clear, actionable goals ensure that every security measure, every mitigation step, and every investment in protection directly strengthens long-term resilience. A structured roadmap secures systems and ensures that cybersecurity decisions help, not hinder business success.
Secure Your Business with Devox Software!
Stage 2. Mapping the Terrain: Where Strategy Meets Action
Cybersecurity is not just about ticking boxes — it’s about taking control. Mapping the terrain is your opportunity to set the terms of engagement and ensure that no vulnerability goes unnoticed and no asset is left unprotected. A structured risk assessment methodology cybersecurity applied by experts ensures that every asset is accounted for, every vulnerability is uncovered, and every potential risk is accurately assessed.
But this phase is about more than just defense — strategy. Identifying what is most valuable and understanding the associated risks lays the foundation for more innovative, proactive decisions. Aligning this phase with NIST cybersecurity assessment guidelines helps organizations prioritize security controls and ensures thorough and actionable assessments.
Think of this as your plan for resilience. When you know what you have, what it’s worth, and where it’s most vulnerable, you can respond to threats and anticipate them. The more detailed your plan is, the stronger and more adaptable your defense will be. Choosing the right approach from the various cybersecurity assessment types allows you to tailor your strategy to your organization’s unique risks, industry regulations, and operational needs.
True cybersecurity strength doesn’t come from being invulnerable — it comes from being prepared. That preparation starts now, on your terms, with a strategy designed for long-term resilience. This is your terrain. Master it.
Stage 3. Spotting Weak Links
Cybersecurity is only as strong as its weakest link — and in most cases, that weak link is external. Nearly two-thirds of security incidents stem from vulnerabilities in third-party relationships, making vendor security a risk that companies can no longer ignore.
A comprehensive cybersecurity program assessment is your first line of defense. It uncovers misconfigurations, outdated software, and hidden vulnerabilities before they grow into full-scale security breaches. The key to this? Preparation. Our data shows that a well-structured assessment process can cut assessment time in half without sacrificing depth or accuracy.
Adequate preparation starts with clear assessment boundaries focusing on high-risk business areas, critical infrastructure, and sensitive data streams. At this stage, stakeholder involvement is non-negotiable. Those closest to day-to-day operations provide invaluable insights into overlooked risks and operational dependencies that may not surface during a routine audit.
However, the proper methodology is just as important. Cybersecurity frameworks such as NIST SP 800-37 and ISO/IEC 27001 serve as a blueprint for aligning teams, ensuring a common security language, and incorporating best practices into your assessment process. The goal? To transform cybersecurity from a reactive necessity to a proactive competitive advantage.
Outsource Security, Optimize Success with Devox Software.
Stage 4. Assessing the Threat Landscape
Understanding risks is one thing — knowing how to mitigate them effectively is another. By using established frameworks such as NIST SP 800-30, we help organizations identify the most critical attack vectors and rank them according to their potential impact. This structured approach ensures that security resources are deployed where they matter most.
Take access control, for example. Nearly 75% of organizations still don’t use multi-factor authentication (MFA) to manage access rights — a significant security gap. We close this gap by enforcing role-based access controls, implementing MFA, performing ongoing access reviews, and continuously monitoring activity. Every access decision follows the principle of least privilege and ensures that users are only granted the permissions required for their specific tasks — no more and no less.
Building a Resilient Security Posture
A cybersecurity maturity assessment helps organizations evaluate how quickly they detect, respond to, and recover from security incidents. We analyze historical response records, assess gaps in incident handling, and refine protocols to ensure a dynamic, adaptable security posture that evolves with new threats. A strong security framework is never static; it must be continuously optimized to safeguard sensitive data in every outsourced relationship.
To support this process, we rely on a cybersecurity risk assessment tool to streamline documentation and ensure that:
- System security plans are clearly defined
- Audit logs and account management protocols are in place
- Incident response procedures are well-documented and actionable
- Contingency plans are established before work begins on-site
Structuring the Cybersecurity Risk Assessment
To streamline the process, we divide the cybersecurity risk assessment into well-structured phases, typically spanning three to four weeks:
- Preparation (1–2 weeks). Establishing communication lines, defining team roles, and determining whether internal teams or external providers will lead the assessment
- Execution. External vulnerability assessment, on-site and remote analysis, remediation, and risk mitigation
- Reporting & Optimization. A detailed security report, remediation roadmap, and final review to ensure long-term resilience
By following this structured approach, we ensure that security controls are correctly enforced, access management remains seamless, and sensitive data is protected at every stage. Whether you need a high-level overview or a detailed cybersecurity risk assessment example to guide decision-making, our methodology delivers clear, actionable insights.
The result? Stronger security, optimized risk management, and the confidence to take on cybersecurity challenges precisely.
Stage 5. Building Resilience Into the Plan
This phase involves developing a remediation strategy that controls critical risks without slowing down operations. Continuous monitoring and updates form a protective shield that will stand the test of time.
Evaluating Key Security Controls
We focus on three core areas that support a strong, resilient security posture. These controls, applied to outsourcing scenarios, protect sensitive data and keep threats at bay.
Infrastructure Review In Action
A quick, thorough infrastructure review sets the tone. Using a mix of well-structured methods and automated tools, we perform comprehensive network security testing — firewall checks, segmentation assessments, and intrusion detection evaluations — to uncover vulnerabilities. We fix problems quickly and close gaps before attackers even try.
System Configuration Analysis
Misconfigurations often need to be corrected. We tackle the problem head-on. We minimize human error and strengthen your defenses by establishing appropriate baselines, monitoring unauthorized changes, and regularly reviewing configurations. Automated tools highlight problems and reduce the risk of costly mistakes.
Cloud Security Assessment
The cloud offers not only more complexity but also new opportunities. We evaluate cloud configurations, logging procedures, and identity architectures with a well-structured cybersecurity resilience assessment methodology to ensure they meet strict security benchmarks. A structured risk assessment process in cybersecurity helps businesses adapt to emerging threats while maintaining seamless operations.
Strengthening Data Protection Practices
Data security strengthens trust and compliance. We classify information according to its sensitivity and ensure that each category receives the right level of protection. Encryption, strict transfer protocols, and careful handling procedures form a tight data shield. Outsourcing relationships receive special attention to ensure that sensitive data is transported securely and remains protected at every stage.
Review Of Security Policies And Procedures
Sound policies and procedures form the basis for reliable security. We review documentation, training programs, and compliance efforts to ensure everything aligns with relevant standards and regulations. Our approach ensures teams have clear guidelines, practical tools, and meaningful metrics to track progress.
Rapid Compliance Audits
With increasing compliance requirements, streamlined compliance is critical. We confirm compliance with industry standards, review documentation, and validate certifications. Bringing in external expertise can help you meet complex requirements and stay ahead of evolving rules — without losing time, money, or credibility. For many organizations, bringing in external expertise reduces cybersecurity assessment cost by streamlining processes and eliminating redundant security expenditures.
Learning From Incident History
Past security breaches and near misses can yield valuable lessons. We analyze incident data to determine where defenses performed well and failed. By measuring response times, investigating root causes, and fine-tuning countermeasures, we help you stay agile, reduce future risks, and maintain smooth operations — even under pressure. This structured approach to assessing the cybersecurity risk of systems ensures continuous improvement — not just in breach recovery but in long-term resilience.
Preparation of The Assessment Report
Finally, we prepare a detailed Security Assessment Report (SAR) that includes key findings, risk levels, and clear recommendations. The report is aligned with your business objectives, focuses on the essentials, and provides an actionable plan. You get a complete overview of your security landscape and practical steps to improve it over time.
Conclusion
Cybersecurity should not be a burden — it should be a competitive advantage. At Devox Software, we do not just help companies assess risk. We strengthen their operations with robust, forward-thinking security strategies.
With our expertise in secure software development, risk management, and compliance, we ensure that your outsourcing partnerships are a pillar of strength, not a vulnerability. Whether you are evaluating vendors, protecting sensitive data, or optimizing security controls, our solutions give you the clarity, confidence, and control you need to act quickly without compromising security.
Cyber threats are relentless. Your defenses should be more substantial. Let us create a security framework that does more than protect — it empowers your business to thrive. Secure your systems, data, and reputation. Schedule your assessment today!